The PGP Horror Story: Lessons in Key Management and Backup Strategies
Introduction:
In the realm of digital security, the loss of encryption keys can be a terrifying experience. Recently, I encountered a PGP (Pretty Good Privacy) nightmare when I realised that my PGP keys were missing after reinstalling Windows on my computer. To make matters worse, I had forgotten to back up my keys, and the keys were set to never expire, I didn’t generated revocation certificate that’s preventing me from revoking them. This meant that multiple outdated keys would be visible to anyone accessing key servers if I created new ones. Determined to rectify the situation, I embarked on a journey to recover my lost keys, only to encounter unforeseen challenges along the way.
The Recovery Mission:
After reinstalling Windows, I connected my old backup hard drive, only to find that it wasn’t being recognised by my computer. Troubleshooting revealed that the SATA power interface on my motherboard was faulty, forcing me to resort to an external SATA to USB cable to access the drive. Unfortunately, I discovered that the drive had been fully formatted (over written with zeros) and repurposed for my Raspberry Pi 4. This realisation left me without any offline backups, intensifying my predicament. Desperate to find a solution, I delved into my cloud storage services, but my efforts yielded no PGP keys. Instead, I stumbled upon an encrypted archive named “backup-20230214154323.tar.gz.gpg”.
A Eureka Moment:
After hours of frustration, a thought suddenly flashed across my mind. What about files with the extension “.asc”? Until that moment, my search had focused solely on “.pgp” and “.gpg” files. My hopes rekindled, I initiated a search for “.asc” files, and to my immense relief, I discovered a crucial backup file.
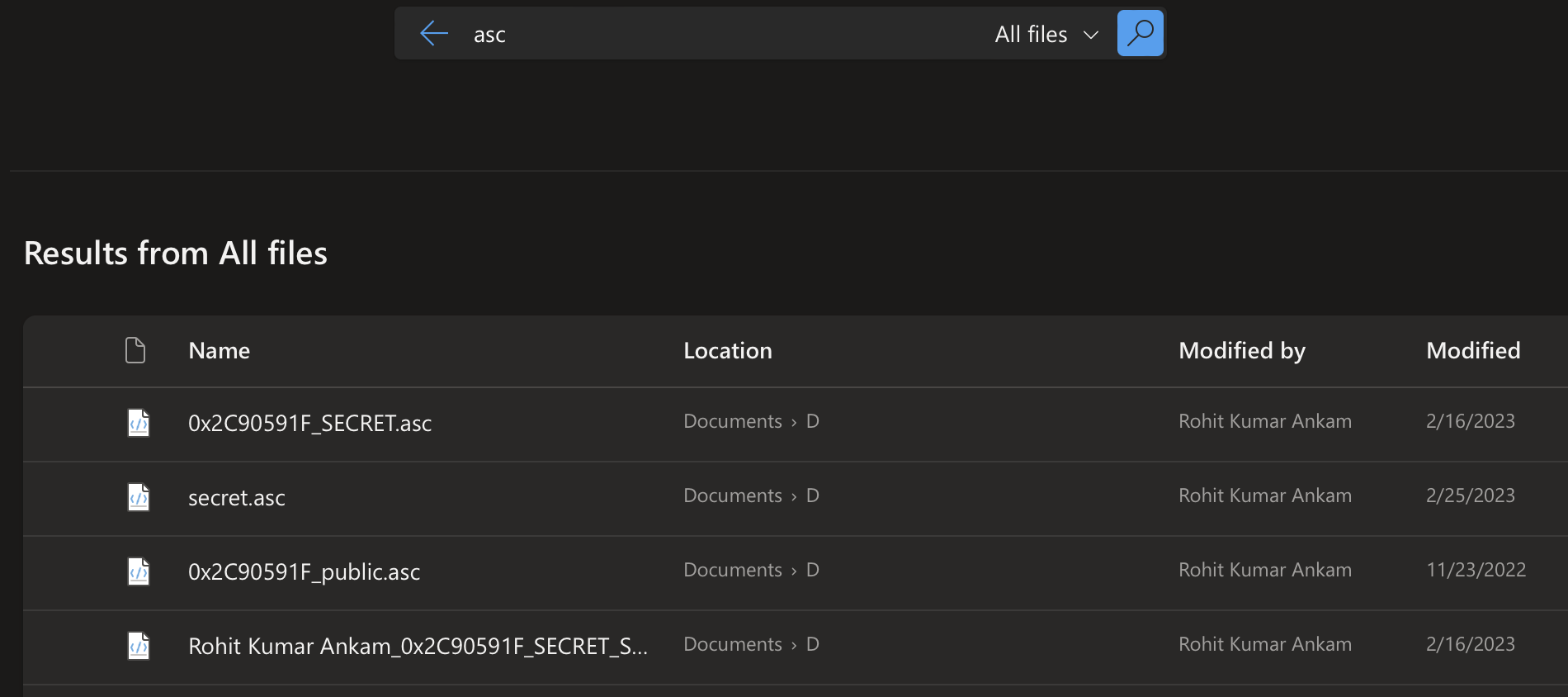
screenshot
The Joy of Preparedness:
As I gazed upon the file, a sense of relief and happiness washed over me. Throughout this ordeal, I had unknowingly maintained a good backup strategy by storing a backup in an unexpected file format. This discovery underscored the importance of thorough preparation and reinforced valuable lessons in key management and backup practices.
Key Learnings:
- Never neglect the generation and safekeeping of revocation certificates for your PGP keys. Store them in an easily accessible location.
- Backup your encryption keys regularly and maintain multiple copies in secure locations.
Valuable Advice:
- Always assign a passphrase to your PGP keys, ensuring an additional layer of protection.
- Set an expiry date for your keys, even if it may seem inconvenient, to mitigate potential risks associated with lost or compromised keys.
Why I Abandoned Self-Hosting and Embraced PGP:
In my personal journey, I made the decision to discontinue self-hosting my email server and transitioned to Office 365 (Exchange) for email hosting. This change not only provided me with a reliable email service but also offered 1 TB of cloud storage, solving my cloud storage needs. I emphasise the importance of encrypting files before uploading them to OneDrive and safeguarding your PGP keys with strong passphrases. It’s worth noting that Microsoft’s scanning practices, aimed at detecting malware/viruses within encrypted zip files (https://infosec.exchange/@threatresearch/110373860063222707), might extend to PGP encrypted files in the future. Additionally, OneDrive proves to be a cost-effective alternative to AWS Glacier in India. It only costs 147.50 INR(~1.78USD) per Month.
Conclusion:
My PGP horror story served as a wake-up call, reminding me of the criticality of effective key management and backup strategies. It highlighted the importance of generating revocation certificates, assigning passphrases, and setting expiry dates for keys. Furthermore, it prompted a reevaluation of my email hosting choices, leading me to embrace Office 365 and its integrated cloud storage solution. By sharing this experience, I hope to inspire others to prioritize the security of their encryption keys and adopt robust backup practices, avoiding potential nightmares like the one I encountered.
* This post is licensed under CC BY-SA 4.0